Web application vulnerability assessment & penetration testing is a key security requirement for a variety of regulatory frameworks, from PCI DSS, SOX, ISO 27001, HIPAA etc…
Generally most organization’s application portfolio relies on a diverse range of platforms and infrastructure that may be extremely susceptible to different types of vulnerabilities. Our Application VAPT services simulates techniques used by hackers to help you identify and address potential threats to your applications. We also implement recommendations such as patch management, functionality analysis and access control to secure your applications.
Network devices are commonly targeted by hackers in order to destabilize the entire network or to steal information. Our Network VAPT services help you validate the configuration of various technology devices & platforms on your network as per best practices. We help you identify security issues and weak links in your network through network assessment, and penetration testing.
Due to a heavy dependency on mobile devices, users tend to store their precious data on it. Mobile technology uses Android or iOS operating systems. Just as any other operating system, the applications created and running on mobile devices are vulnerable too, the Android Platform has been a favorite battlefield of worldwide hackers since its inception there are many hackers with malicious intent that can and do break into an Android device to steal valuable personal information or to profit from illegal financial transactions.
Hence all applications running on a mobile device pose a bigger security threat to the data because of the following reasons.
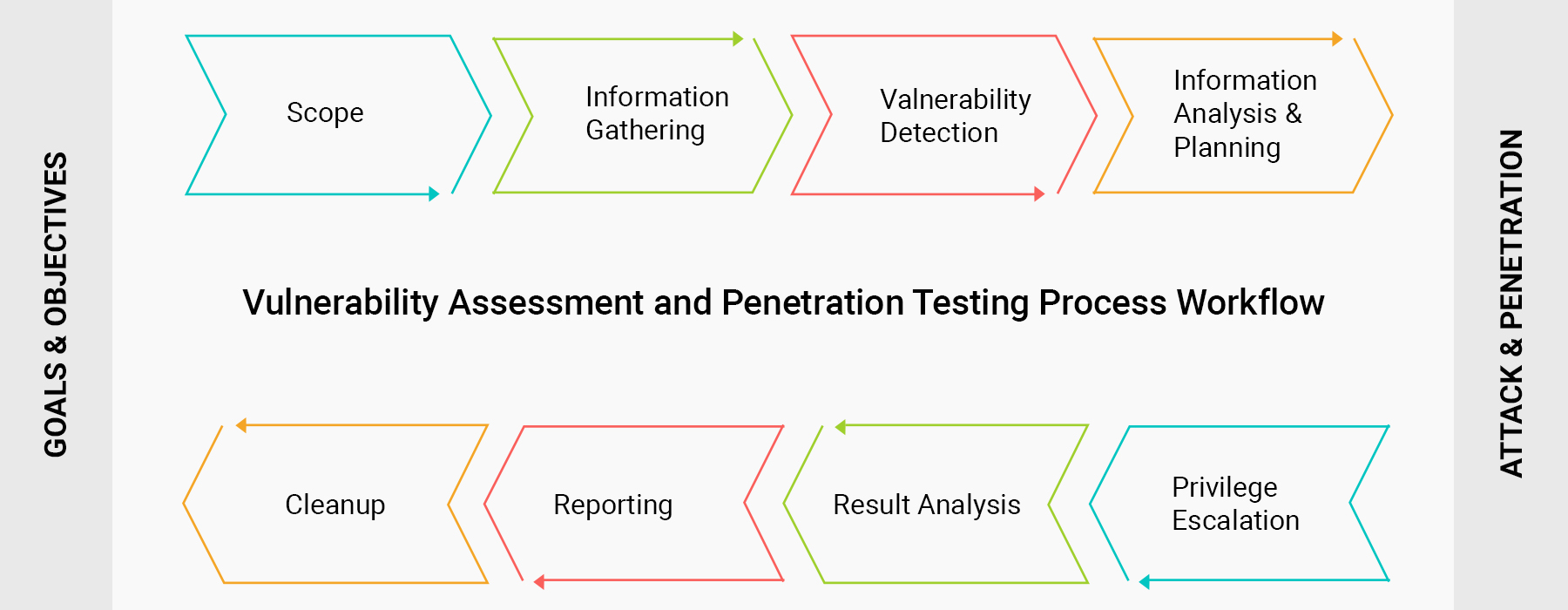
Vulnerability Assessment:
Vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a hardware, software, database and network devices. In addition, vulnerability assessment can forecast the effectiveness of proposed countermeasures and evaluate their actual effectiveness after they are put into use.
Vulnerability assessment consists of several steps
Vulnerability Assessment and Penetration Testing (VAPT) approach gives an organization a more detailed view of the threats facing its applications, enabling the business to better protect its systems and data from malicious attacks.
Penetration testing (also called pen testing) is the practice of testing hardware, software, database and network devices to find vulnerabilities that an attacker could exploit. The main objective of penetration testing is to determine security weaknesses.
Pen tests can be automated with software applications or they can be performed manually. Either way, the process includes (reconnaissance) gathering information about the target before the test, identifying possible entry points, attempting to break in (either virtually or for real) and reporting back the findings.
When searching for vulnerabilities in websites and web apps, it is mistakenly assume that automated penetration testing tools can fulfill all these requirements. But in truth, no automated vulnerability scanning solution can find every type of vulnerability. Certain kinds of authorization issues or business logic flaws will only show up during manual web application penetration testing.
Before initiating manual web application penetration testing, Avanté consultants scans applications with automated tools to ensure consistent results and then uses manual testing to find flaws that automated tests can’t discover.
Manual web application penetration testing is most effective and cost-efficient when combined with other scanning technologies. Manual testing on its own can be quite expensive and time-consuming, taking weeks to perform a full penetration test.